CONTÁCTENOS
info@bidaiondo.com

Quishing: qué es, cómo funciona y cómo evitar y protegerte de este tipo de ciberestafa

Vamos a explicarte qué es el quishing, un tipo de estafa parecida al phishing, pero que se basa en engañarte mediante códigos QR. Se trata de una estafa en la que hacen pasar un código por legítimo, y te llevan a una web donde robarte datos.
Vamos a explicar este artículo explicándote qué es exactamente el quishing, y sus principales características. Esto va a hacer que seas capaz de identificarlo y diferenciarlo de otros tipos de estafa, y saber su existencia es el primer paso para protegerte de él. Después, te diremos algunos consejos básicos para intentar evitar caer en este tipo de trampas.
Qué es el Quishing y cómo funciona
El término squishing viene de QR phishing, o lo que es lo mismo, phishing mediante QR. Esto es así porque es un tipo de estafa basada en lanzar cebos como la pesca o el phishing, pero el cebo que se utiliza en este caso es un código QR que las víctimas deben escanear.
Un código QR es un código compuesto por cuadrados blancos y negros, que forman una especie de dibujo ilegible. Es una especie de atajo, y si apuntas hacia él con la cámara del móvil o una aplicación para leer códigos QR, se generará un enlace web al que está apuntando.
La cuestión ya no es solo difundir un código QR que te lleve a una página fraudulenta, porque si encuentras uno de estos códigos por la calle y te lleva a una web donde debes introducir los datos es evidente que es una estafa. Lo que hacen los cibercriminales en este caso es trabajárselo un poco, igual que suelen hacer con el phishing por SMS o smishing.
En el caso de esta estafa, es intentar hacer que el código QR sea legítimo y que parezca que pertenece a una empresa real y conocida. Esto lo pueden hacer con tarjetas de visita, papeles publicitarios o mediante imágenes de Internet en las que se te habla de una oferta.
El código apuntará a una web fraudulenta que es una copia de la página real a la que supuestamente está apuntando el código. En esta web te pedirán datos personales, como los datos de acceso de una de tus cuentas de Internet o directamente datos de tu tarjeta de crédito.
Imagínate por un momento que te encuentras un papel en el que se te dice que vas a conseguir una tarjeta de regalo de Amazon. Este papel tiene un código QR, y esto te lleva a una web en la que debes identificarte con tus datos de Amazon, o directamente con tu tarjeta bancaria. Y de esta manera, te han engañado para regalar tus datos, lo que en algunos casos puede llevar a que te roben dinero.
Cómo evitar caer en este tipo de estafa
El primer paso para evitar estas estafas es desconfiar de los códigos QR que te lleguen sin pedirlos o de una fuente que no sea fiable. También desconfía de esos que aparecen por la calle o los que directamente te prometen cosas u ofertas que son demasiado buenas para ser verdad.
Por eso, antes de escanear un código QR, debes intentar verificar la fuente. Mira el folleto o cartel, o la pegatina donde está el código QR. Si es algo que te encuentras por la calle ya sabes que no va a ser real, pero si es algo que te han metido en el buzón, desconfía siempre. Vamos, que debes intentar tener muy claro que es algo legítimo, aunque si tiene un QR para ocultar la web a la que te lleva debes desconfiar casi por reflejos.
Lo normal es que solo por escanear un código QR no pase nada. Sin embargo, hay veces en las que los atacantes jugarán con tu curiosidad e intentarán que la web donde se te lleva te haga picar. También es posible que se te descargue algún archivo peligroso en el dispositivo o virus, y se te diga que lo uses para alguna cosa... cuando en realidad es para infectarte.
Cuando entres en la web a la que apunta un código QR, revisa siempre la URL o dirección de la página. Así, podrás comprobar si la página en la que entras es la real o es otra con un nombre completamente diferente. A veces en la web a la que se te lleva pueden utilizar una palabra que sea el nombre de la empresa, por lo que conviene saber cuál es la dirección real para no caer en la trampa de entrar en páginas con nombres parecidos, pero que no son la oficial.
Hoy en día, casi todas las aplicaciones nativas de cámara de los móviles tienen un escáner QR. Sin embargo, también es conveniente usar alguna app especial de escáner de QR que tenga protecciones de seguridad. Algunas tienen esta característica para detectar enlaces maliciosos y advertirte antes de entrar en la web a la que se apunta.
Y por último, también conviene tener actualizada la seguridad de tu móvil. Asegúrate de que el sistema operativo esté actualizado, y si tienes alguna protección que puedas activar contra webs maliciosas o descargas dañinas, asegúrate de tenerlo todo activo.
https://www.xataka.com/basics/quishing-que-como-funciona-como-evitar-protegerte-este-tipo-ciberestafa
Noticias
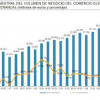
El comercio electrónico en España registra su mayor crecimiento desde 2022 (+22,6%).
Ahora podrás incluir enlaces internos en tus Instagram reels: descubre las últimas novedades de Edits.
Sistemas de comercio online
 Le mostramos la mejor forma de comercializar productos y servicios online, mediante un servicio profesional de instalación, gestión y mantenimiento de su tienda virtual,
Le mostramos la mejor forma de comercializar productos y servicios online, mediante un servicio profesional de instalación, gestión y mantenimiento de su tienda virtual,
Programamos a tu medida
 Le ayudamos a alcanzar la excelencia operativa en todos sus procesos de negocio, sean procesos productivos, logísticos, de servicio o de oficina. Además, le aseguramos mantener una mejora continua en su gestión.
Le ayudamos a alcanzar la excelencia operativa en todos sus procesos de negocio, sean procesos productivos, logísticos, de servicio o de oficina. Además, le aseguramos mantener una mejora continua en su gestión.
Artículos Bidaiondo
Amazon quiere escuchar tus conversaciones para ofrecer asistencia personalizada con IA

En julio de 2025, Amazon expandió su cartera de productos de inteligencia artificial al adquirir Bee, la startup detrás del dispositivo “wearable” de IA homónimo que funciona como un asistente personal en segundo plano, escuchándote durante tu día a día y transformando información relevante en recomendaciones, recordatorios y demás acciones proactivas. Ahora, Maria de Lourdes...
10 ideas de negocio que los marketers pueden lanzar hoy con IA.

Los perfiles de marketing parten con una ventaja clara a la hora de lanzar negocios digitales: entienden al cliente, saben validar ideas y dominan los canales de captación. En un contexto donde la automatización y la IA ya están al alcance de cualquiera, la diferencia no está en la tecnología, sino en saber convertir una necesidad real en un modelo de negocio viable. Ideas de negocio digitales basadas en auto...

NOSOTROS
ARCHIVOS
Bienvenido a Bidaiondo, estimado usuario
Utilizamos cookies propias y de terceros para analizar el uso del sitio web y mostrarte publicidad relacionada con tus preferencias sobre la base de un perfil elaborado a partir de tus hábitos de navegación (por ejemplo, páginas visitadas). Política de cookies
Entonces, ¿quiere saber más?
La privacidad de los datos parece importante para usted, y lo es para nosotros también. Guardamos los datos de los cookies durante 13 meses. Si desea conocer más, puede visitar nuestras páginas Política de privacidad y Política de cookies.¿Sabe qué son las cookies? Las cookies son archivos que utilizan prácticamente todas las webs. Al navegar por nuestra página se instalan en su navegador o dispositivo para asegurar que la web funciona correctamente y almacenar información sobre su visita. Los datos que nos proporcionan las cookies tratan al usuario de forma anónima y en ningún caso almacenan información personal.
Los datos que recopilan las cookies que utilizamos son:
- Direcciones IP
- Referencias de páginas visitadas
- Referencias de archivos descargados
- El propio sitio web www.bidaiondo.com
- https://www.moz.com
- https://secure/europeanssl.eu

 inglés
inglés













